I had some issues connecting to vCenter after Configuring ADFS as an Identity Provider with DUO Security for MFA.
Some of the errors i received were:
New-OAuthSecurityContext The OAuth authorization grant redirect response did not provide an authorization code.
New-OAuthSecurityContext The OAuth authorization grant redirect response did not provide an authorization code.
New-OAuthSecurityContext Failed to issue OAuth2 access token.
The received resource parameter is invalid. The authorization server can not find a registered resource with the specified identifier
New-VISamlSecurityContext Failed to retrieve SAML bearer token: An error occurred while sending the request.
Failed to issue OAuth2 access token. MSIS9614: The refresh token received in ‘refresh_token’ parameter is invalid. Error code: invalid_grant
MSIS9622: Client authentication failed. Please verify the credential provided for client authentication is valid. Error code: invalid_client
New-OAuthSecurityContext: Parameter set cannot be resolved using the specified named parameters. One or more parameters issued cannot be used together or an insufficient number of parameters were provided.
It turned out I was missing Configuration steps and using the wrong values in the login script.
*This was setup on vCenter Appliance version 7.0 Update 2c with ADFS 2019 IDP and validated using a Windows 10 VM Logged in as the privileged user Running Powershell 5.1.17763.2183 and VMware PowerCLI 12.4.0 build 18627050
If not already done Install and Configure DUO MFA for ADFS https://duo.com/docs/adfs
Configure vcenter for ADFS IDP by following the Vmware Guide. https://docs.vmware.com/en/VMware-vSphere/7.0/com.vmware.vsphere.authentication.doc/GUID-C5E998B2-1148-46DC-990E-A5DB71F93351.html
(in ADFS don’t forget to configure an Access control Policy and assign it on the webapi configuration of the vcenter application group)
Make sure ADFS IDP authentication with DUO is working Before following the next steps to setup Powercli access.
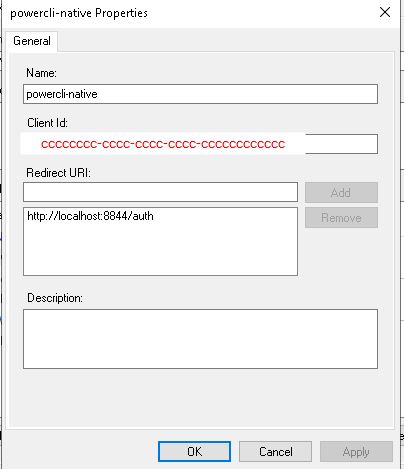
In ADFS Create new Native Application name powercli-native Note the Client ID (cccccccc-cccc-cccc-cccc-cccccccccccc)
Add the Redirect URI: http://localhost:8844/auth
Click OK
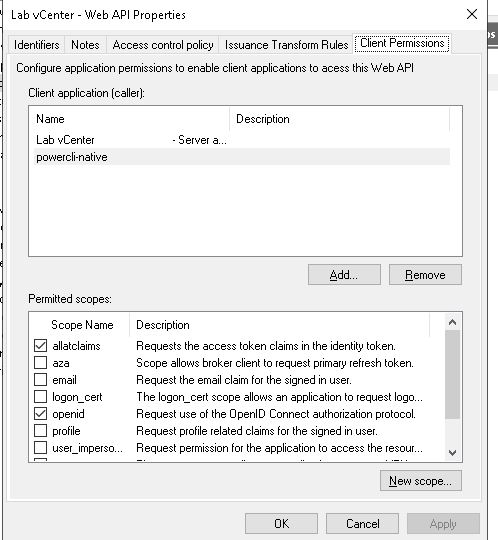
Select the Application under WebAPI, click Edit
Select Client Permissions Tab:
Add Powercli-Native Application Created above
Make sure allatclaims and OpenID are selected.
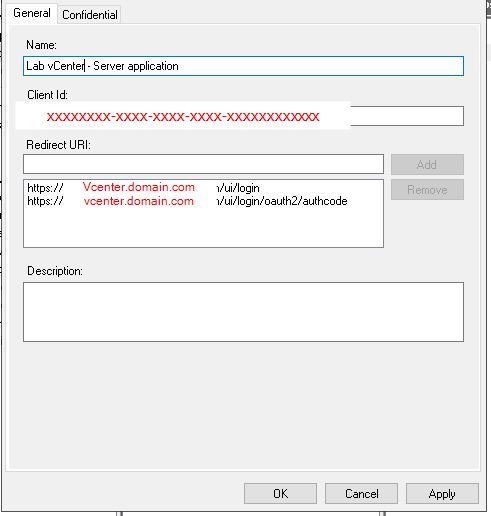
Select Application Under Server Applications, Note Client ID (xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx)
This was validated using a windows 10 VM Logged in as the privileged user Running Powershell 5.1.17763.2183 and VMware PowerCLI 12.4.0 build 18627050
The following script was found on this post (I have added comments inline)
#Vcenter Server FQDN
$VCenterServer = 'VCENTER.DOMAIN.COM'
#ADFS Token Endpoint URL (if you have changed from default then adjust accordingly)
$TokenEndpointURL = 'https://ADFS.DOMAIN.COM/adfs/oauth2/token/'
#ADFS Auth Endpoint URL (if you have changed from default then adjust accordingly)
$AuthEndpointURL = 'https://ADFS.DOMAIN.COM/adfs/oauth2/authorize/'
#Powercli Redirect URL you do not need to change
$RedirectURL = 'http://localhost:8844/auth'
#Enter the Client ID we gather earlier from the powercli-native Native Application
$ClientID = 'cccccccc-cccc-cccc-cccc-cccccccccccc'
#Enter the Client ID from the Server Application We Gathered Earlier
$OAuthResource = 'xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx'
if ( !$OAuth ) { $OAuth = New-OAuthSecurityContext -TokenEndpointUrl $TokenEndpointURL -AuthorizationEndpointUrl $AuthEndpointURL -RedirectUrl $RedirectURL -ClientId $ClientID -OtherArguments @{ "resource" = "$OAuthResource" } }
#If you are using a self-signed certificate use the -IgnoreSslValidationErrors Switch
if ( !$Saml ) { $Saml = New-VISamlSecurityContext -VCenterServer $VCenterServer -OAuthSecurityContext $OAuth -IgnoreSslValidationErrors }
#if this is a standalone remove the -AllLinked Switch
if ( !$Conn ) { $Conn = Connect-VIServer -Server $VCenterServer -SamlSecurityContext $Saml -AllLinked }If the commands complete successfully you should get a Web Browser popup for ADFS/DUO Auth, and Then you should be logged into vcenter. All other commands should work as normal.
Hope this helps someone.